ESAM Multi-function of the most secure embedded module
What is ESAM?
ESAM (Embedded Secure Access Module) is the Embedded security control Module.ESAM hardware has a sensor (voltage, clock, temperature, light, filter (prevent rush/burr), independent of the internal clock (CLK), (SFI) detection mechanism, passive and active shield, glue logic (difficult to reverse engineer circuit), handshaking circuits, high density multi-layer technology, with a metal shield protection layer, to detect internal data self-destruct after external attack, encryption, virtual address bus and the memory chip tamper-proof design, unique serial number and hardware error detection, random number generator, the silicon power analysis and so on security structure,With anti-detection, anti-attack, self-destruct and other hardware security features.ESAM chip operating system has the characteristics of secure file key storage, perfect security mechanism, standard encryption algorithm and so on.
The application of ESAM security module is related to a variety of special or general intelligent devices. For all the products and application systems requiring high data security requirements such as identity authentication, data encryption/decryption, safe storage, communication confidentiality and so on, ESAM embedded security control module can play its unique role in security control.It has two - way identity authentication, data encryption and decryption, decentralized key export, internal decentralized key, digital signature, electronic wallet, transmission line protection, data security storage and other functions.
Applications of the ESAM security module include:
1) Smart card meter: smart card electricity meter, water meter, gas meter, heat meter, etc.;
2) Communication equipment: encrypted Modem, encrypted fax machine, encrypted multiplexer;
3) Financial equipment: encryption password keyboard, financial POS machine, payment password, bank password box;
4) Tax-controlled equipment: tax-controlled taxi meter, tax-controlled refueling machine, tax-controlled cash register;
5) Traffic toll: parking meter, bus toll terminal, vehicle-mounted road and bridge toll terminal equipment;
6) Conditional reception: TV set-top box (STB), PC receiving card, add and de-disturb front end/terminal equipment;
7) Network security: LAN management, login, folder encryption, software protection;
8) Other equipment: smart card water dispensers, smart card charging air conditioners, Internet TV and other equipment.
Key feather
· Adopt high-end secure smart card dedicated secure microprocessor as the hardware platform;
· The internal chip operating system COS adopts TIMECOS, which is the first COS with independent intellectual property rights in China, and the cumulative usage is huge
With over 400 million pieces, it enjoys a high security reputation in the domestic smart card industry.
· Comply with ISO7816, EMV, GSM, PBOC and other international standards and industry standards;
· Support multi-level file structure, can establish a three-level directory, suitable for the requirements of one card and multi-purpose, support binary, fixed-length records,
Variable length records, circular records, wallet records and other file types;
· Supports symmetric algorithms DES/3DES, MAC, high-end chips support asymmetric RSA/ECC algorithm, compatible with symmetric algorithms;

Implementation method
(FYI)
1, key installation
● Application software needs to install: authentication key SK (or decentralized key)
The application software should have DES and an algorithm for generating random numbers
● Installation in ESAM: authentication key SK '(or disperse key) or an important parameter for program execution
2. Software certification process
● Apply software to generate random numbers
● Send random number to ESAM for encryption and return the result X '=DES(SK',RND)
● The software calculates the authentication code X=DES(SK,RND) with its own decentralized key
● Software comparison

Security features
· The chip hardware security has obtained ITSECEAL Level 5 certification;
· Chip tamper-proof design, unique serial number, with measures to prevent SEMA/DEMA, SPA/DPA, DFA and timing attacks;
· Various safety detection sensors: high and low voltage sensors, frequency sensors, filters, optical sensors, pulse sensors,
Temperature sensor, with sensor life test function;
· Bus encryption, with active shielding layer, internal data self-destruct after external attack is detected;
· True random number generator: it is generated by electromagnetic white noise inside the chip and will not be repeated;
· Hardware encryption coprocessor: internal hardware logic circuit realizes symmetric algorithm 3DES, asymmetric algorithm RSA or ECC, plus solution
High density speed.
Success cases:
China Gas
Hikvision
Hunan Expressway Toll Station
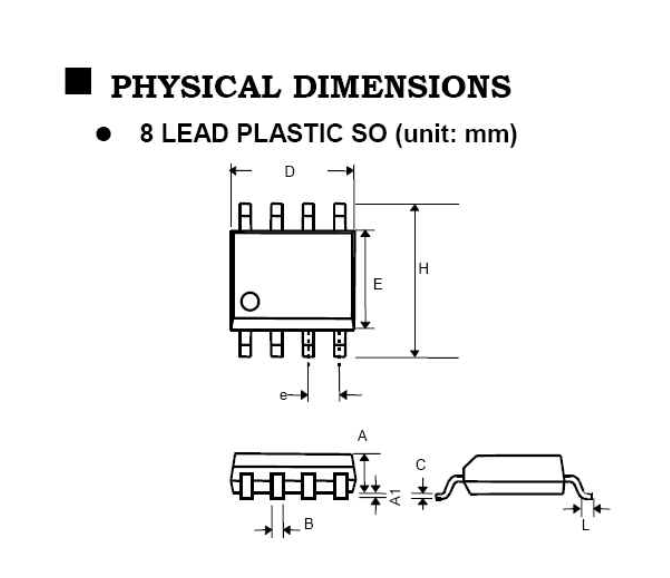
ESAM CPU Cards ESAM Access control security module Esam E-wallet security module SOP package or PVC CR80 Cards package
Contact us now!